Configurable SSO for Microsoft Active Directory (OIDC)
Introduction
The Microsoft Single Sign-On (SSO) integration (OIDC Services) with Keka HR allows employees to log in securely using their Microsoft SSO credentials. This setup simplifies access management and ensures a seamless authentication experience. Follow the steps below to configure Microsoft Azure Directory SSO (OIDC SSO) with Keka.
Only users with "Global admin" role in Keka can configure this setting
Steps
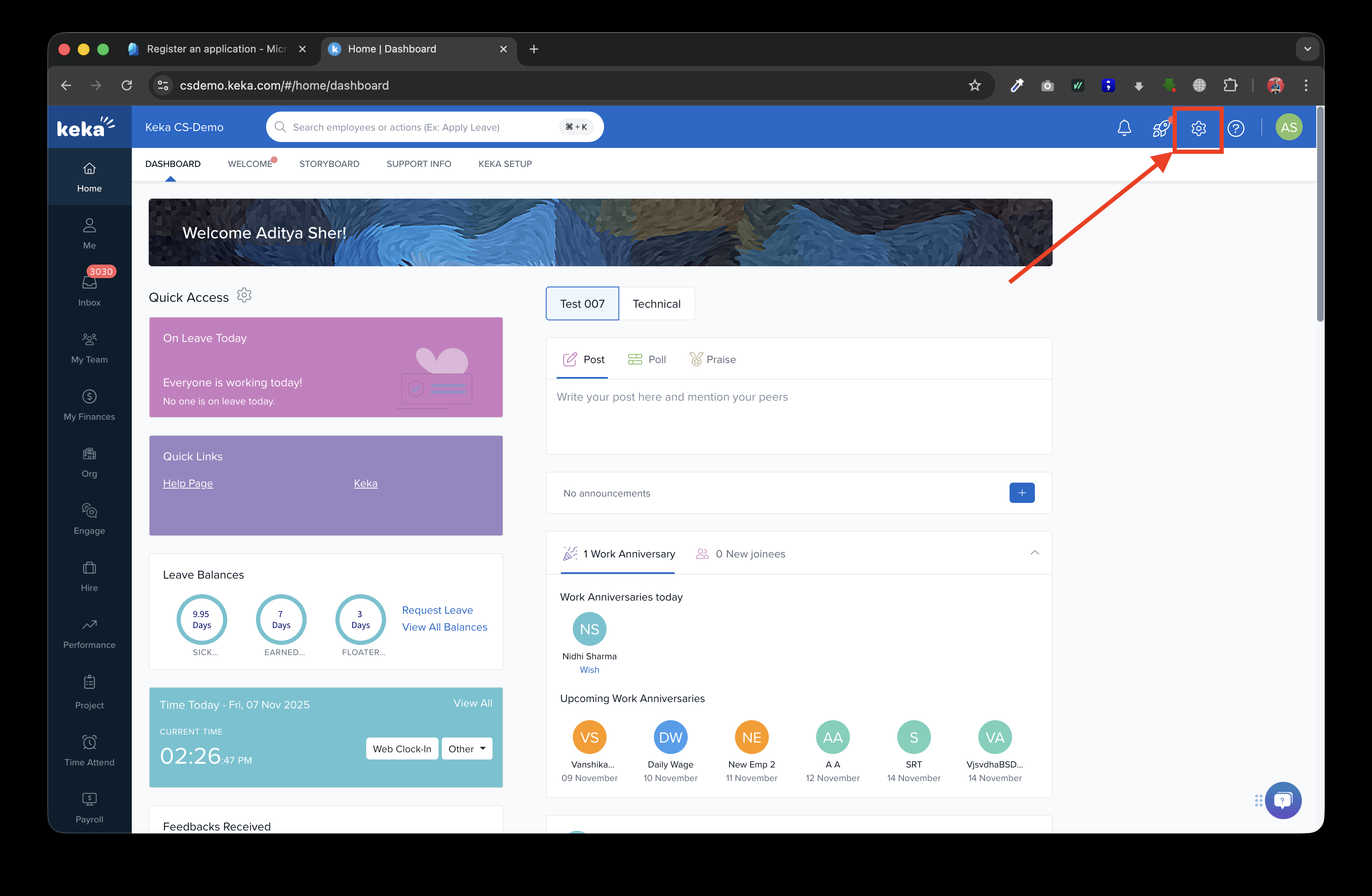
- Open your Keka Account and go to Settings -> Integrations and Automations -> Authentication tab
-
-
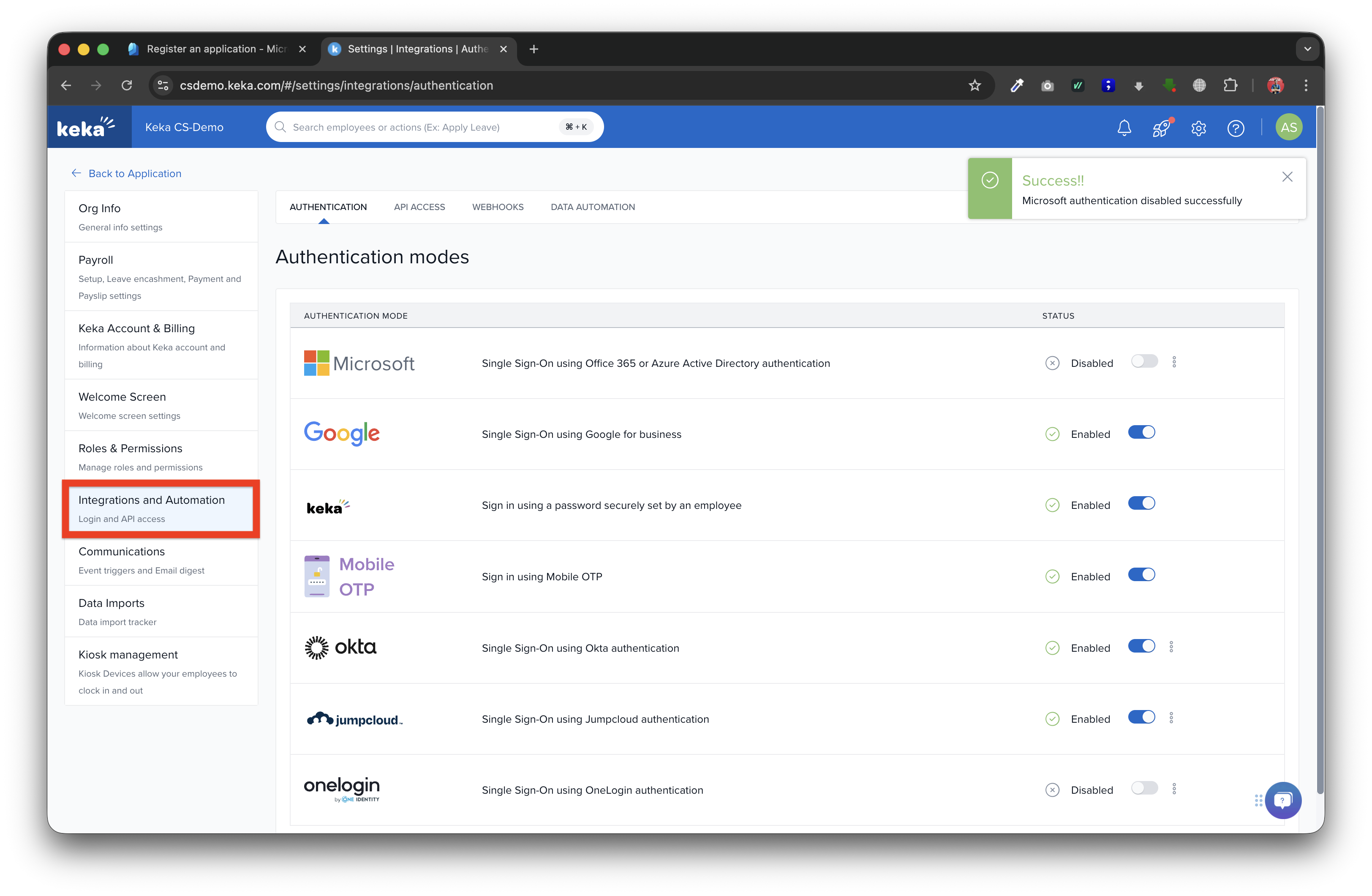
Enable Microsoft Single Sign-on, Select "Custom Active Directory OIDC" option
-
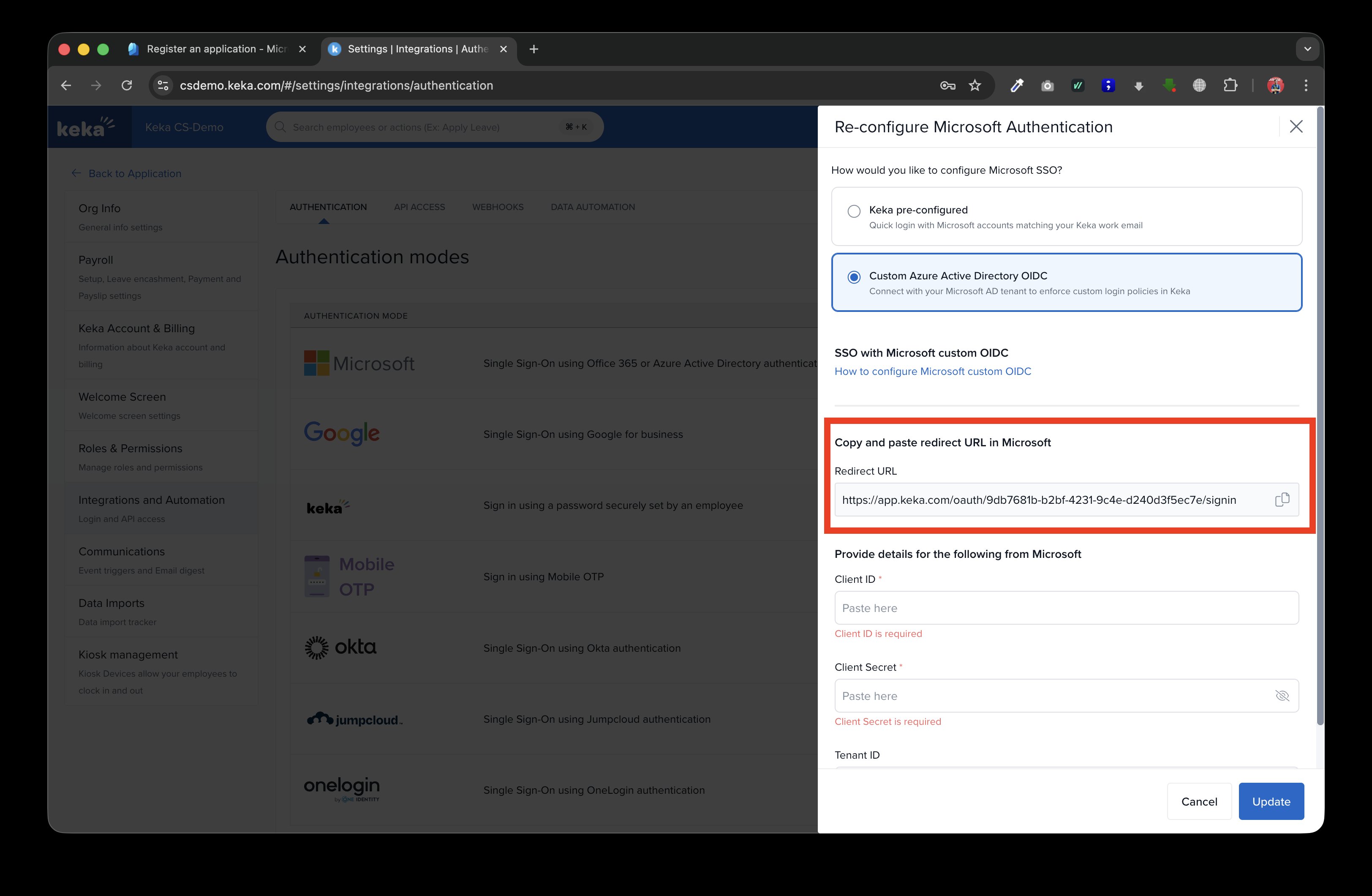
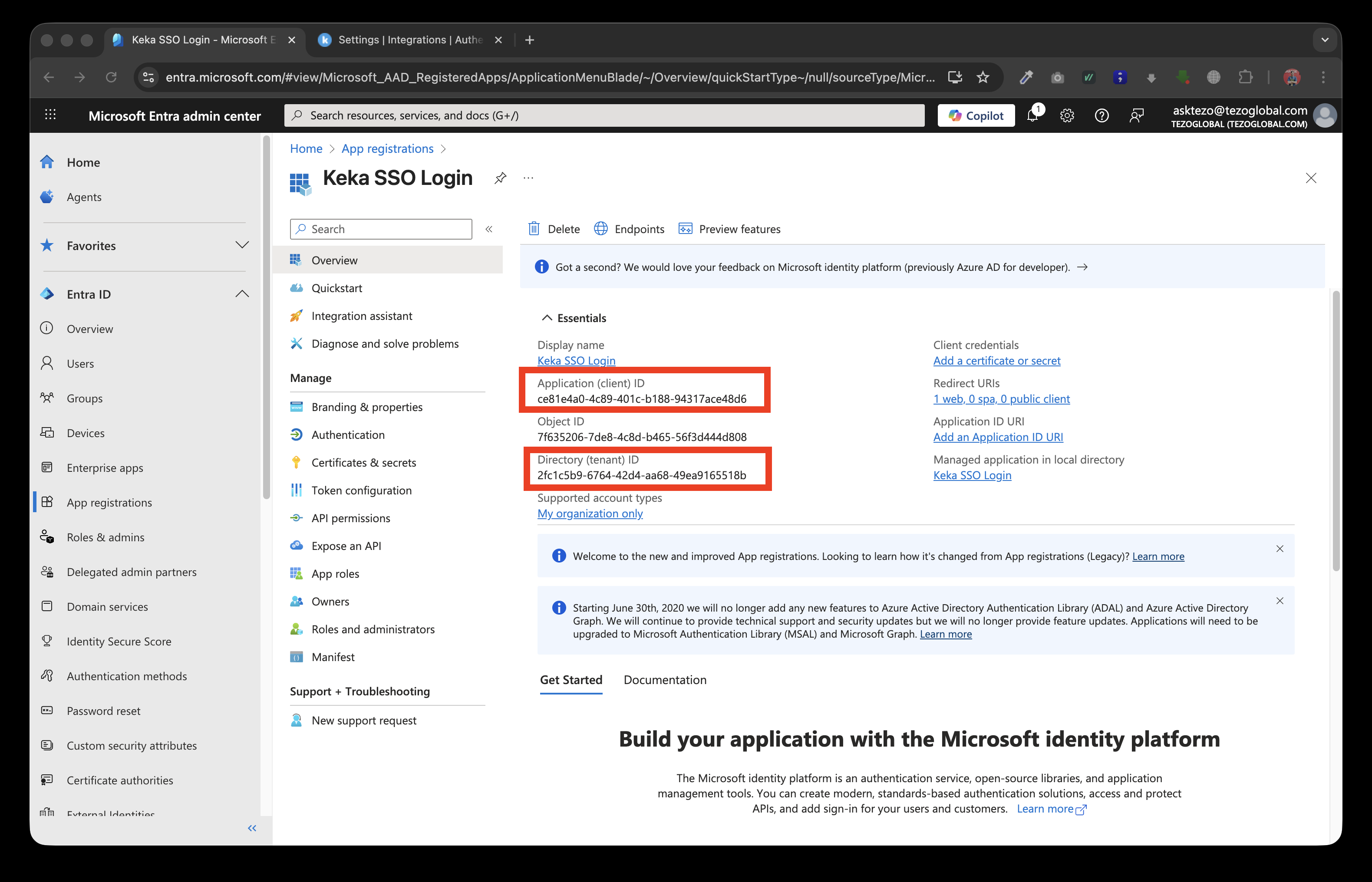
Copy the Redirect URL to add it to Microsoft Active Directory portal.
-
-
Login to Microsoft Active Directory
-
Go to Enterprise Apps
- Click on new registration
-
-
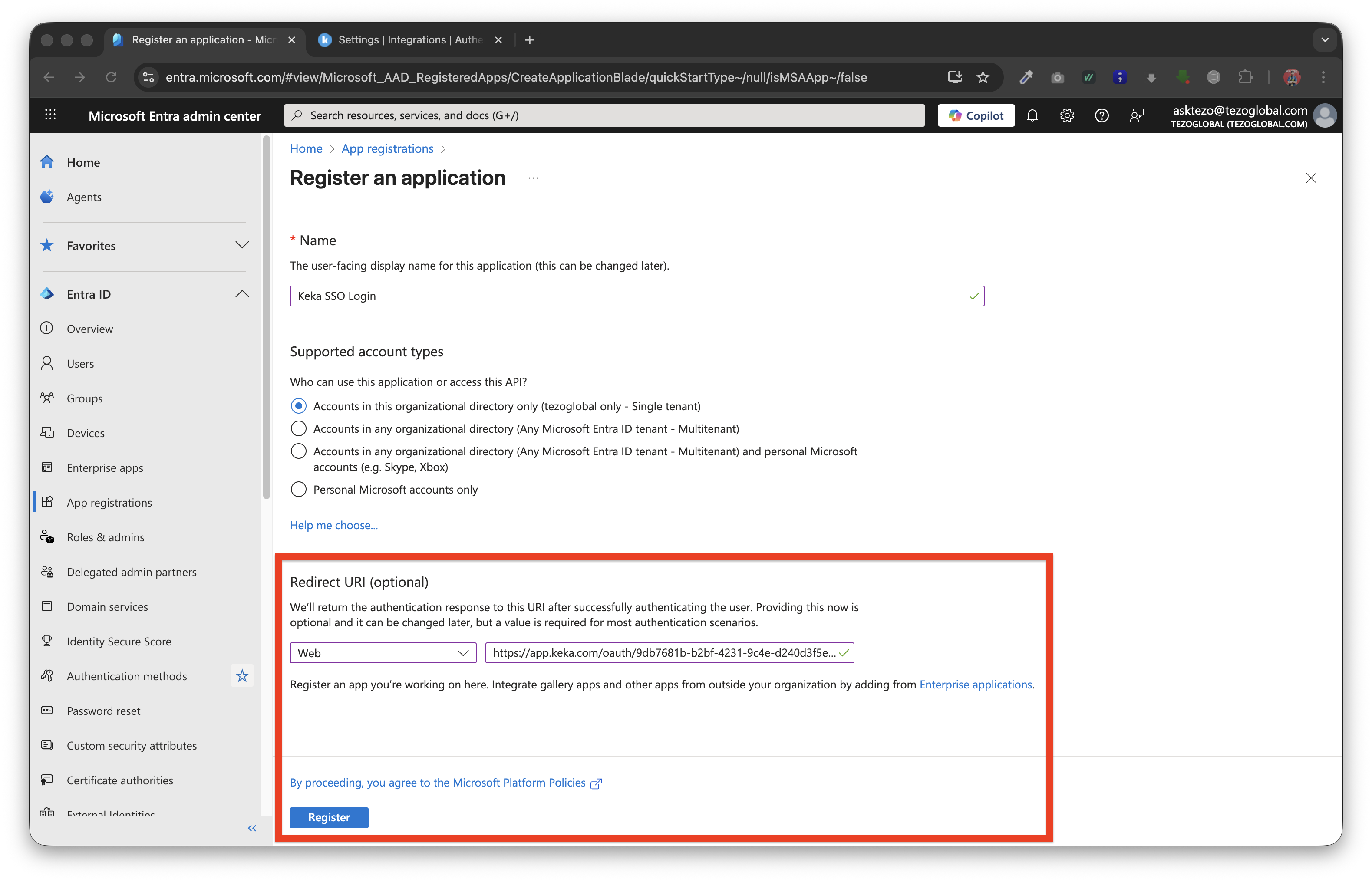
Add an application name and select "Web" option, add the "Redirect URI" copied from Keka Integration tab in Step 5
-
Click on Register after adding the inputs in the above step
-
-
Copy the Tenant ID and Application (client) ID from the application after clicking register
-
-
Click on the Certificates & Secrets tab in AD Portal
- Click New client Secret to generate a new client secret
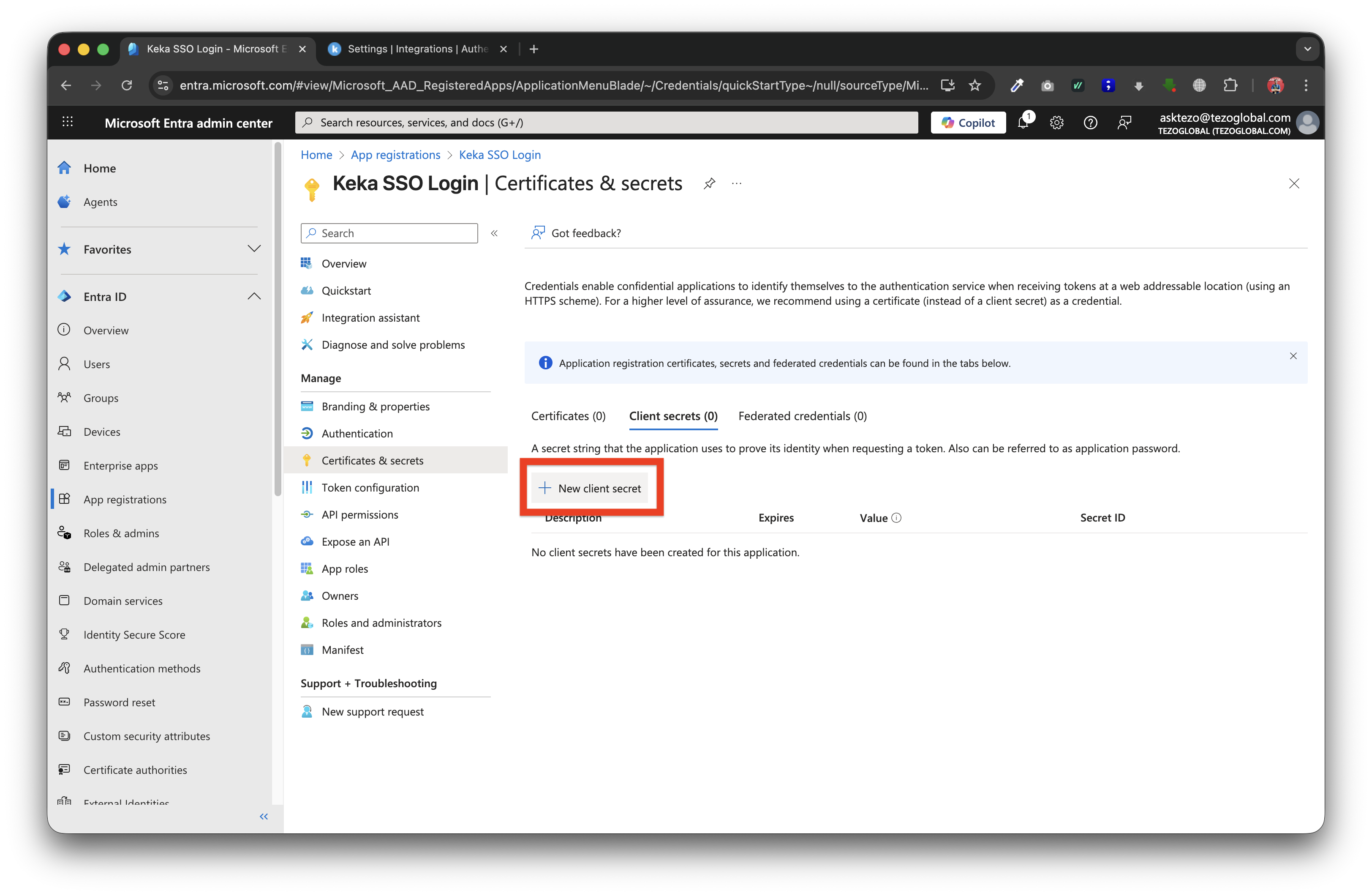
-
Add the required description of the secret and the Expiry as per your organisation policies
-
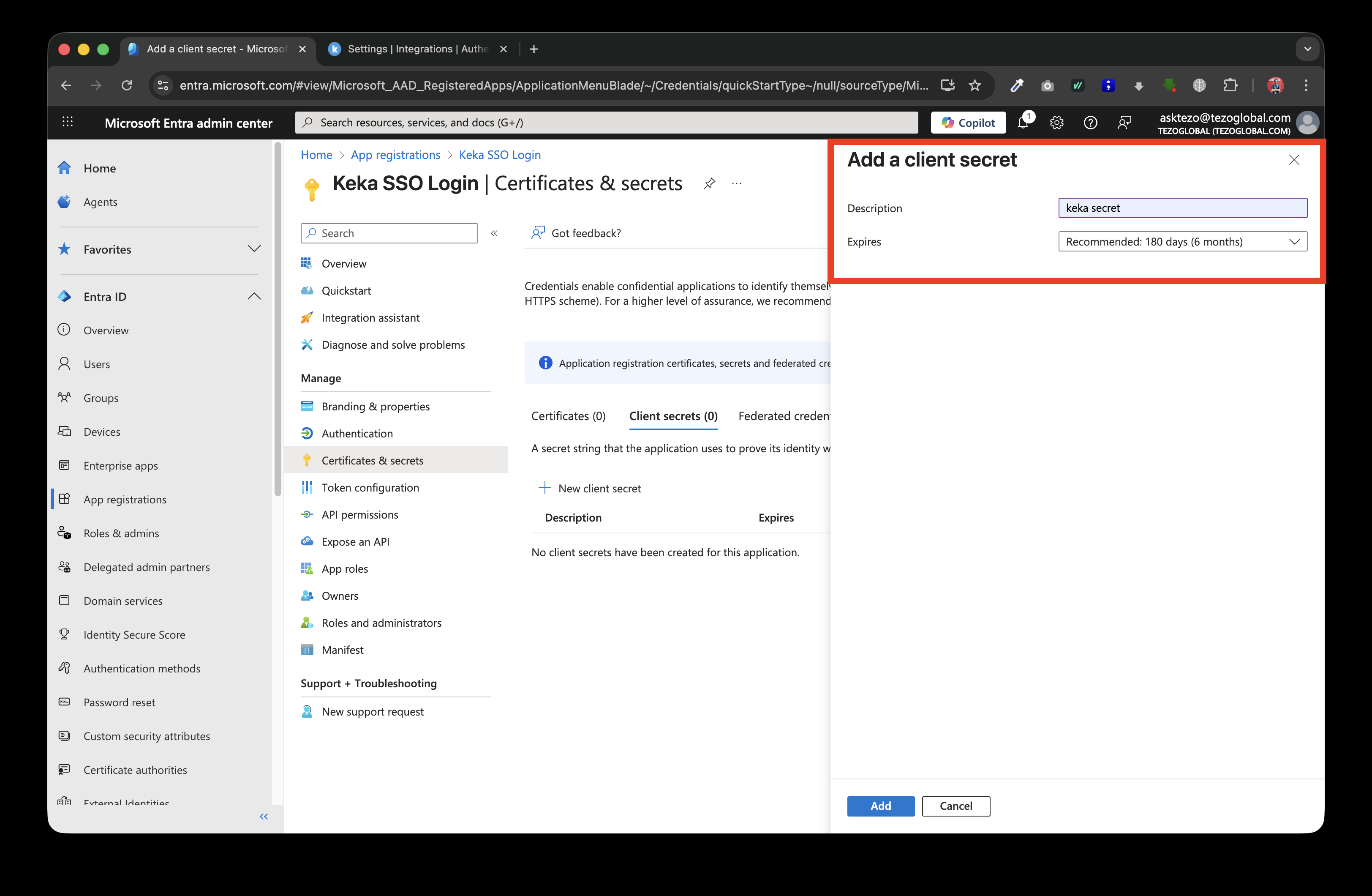
Click "Add" and then copy the secret value
-
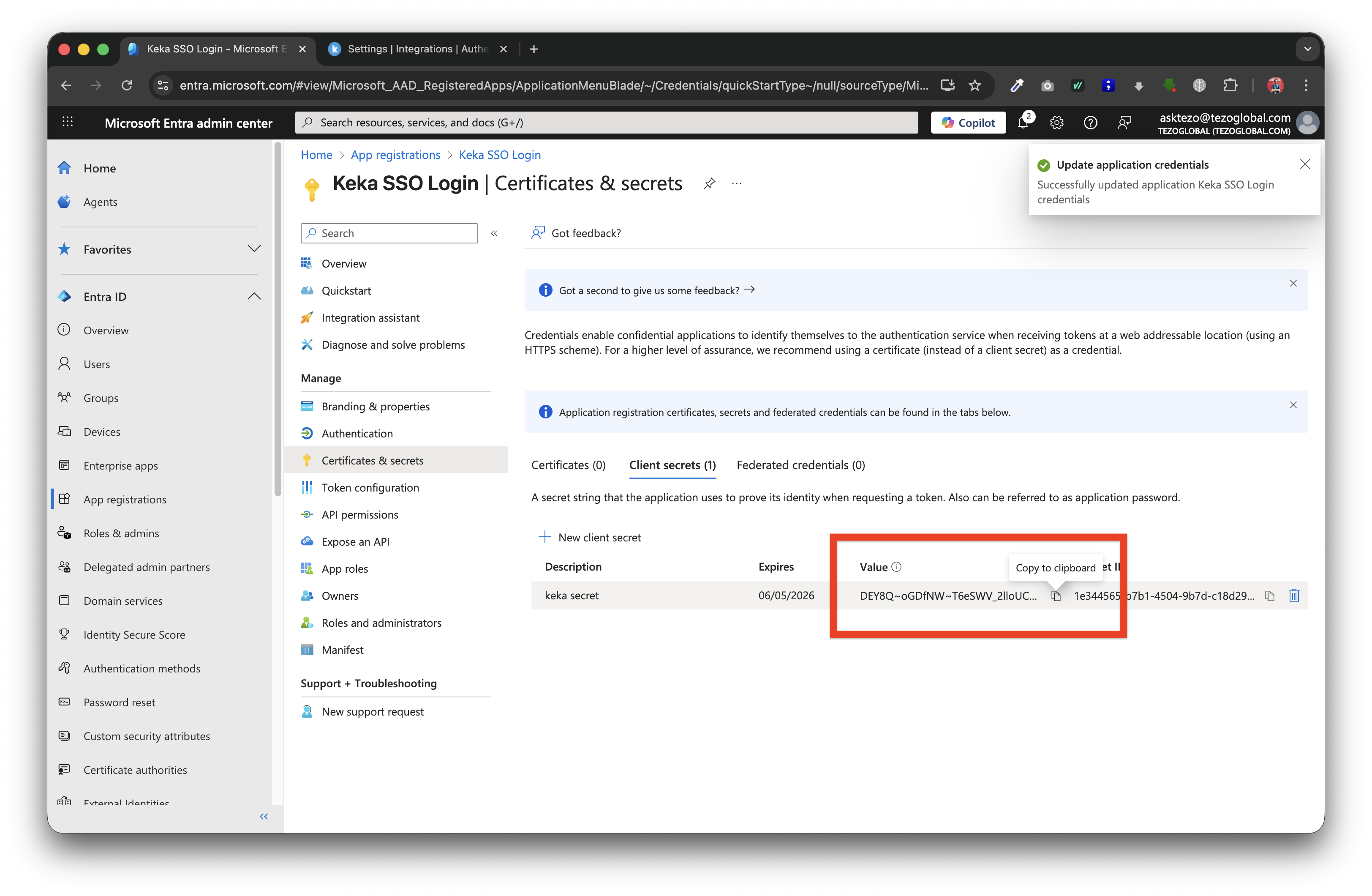
-
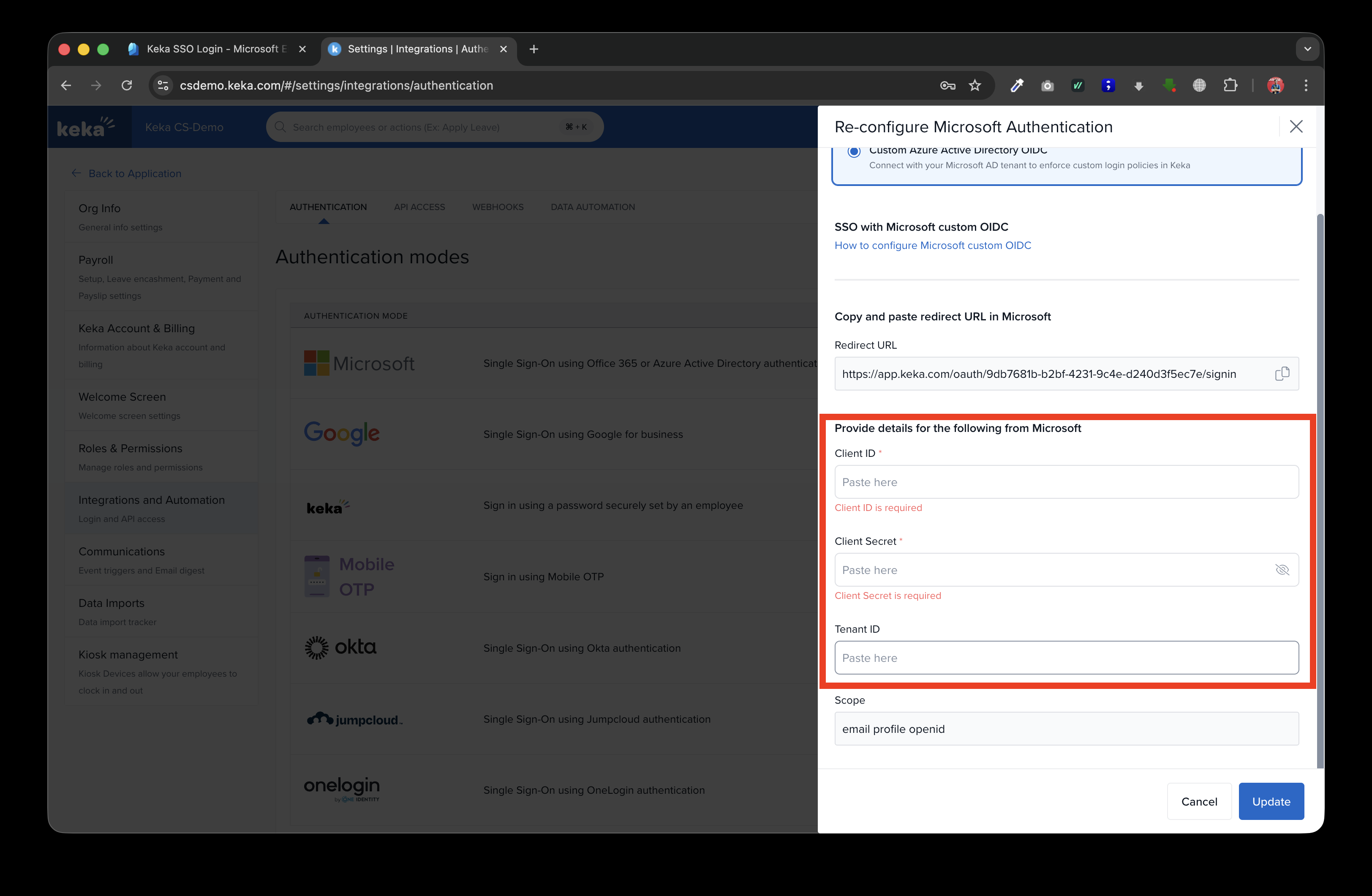
Now go back to Keka, and paste the copied "Tenant ID", "Client ID" and "Secret Key" into the respective fields.
-
-
Click "Update" after adding the values and Microsoft Custom SSO should be enabled for your employees now
For organisations where Azure Active Directory connections require admin approval please follow the below steps to approve login for your app
-
If your employees see this screen before login:
-
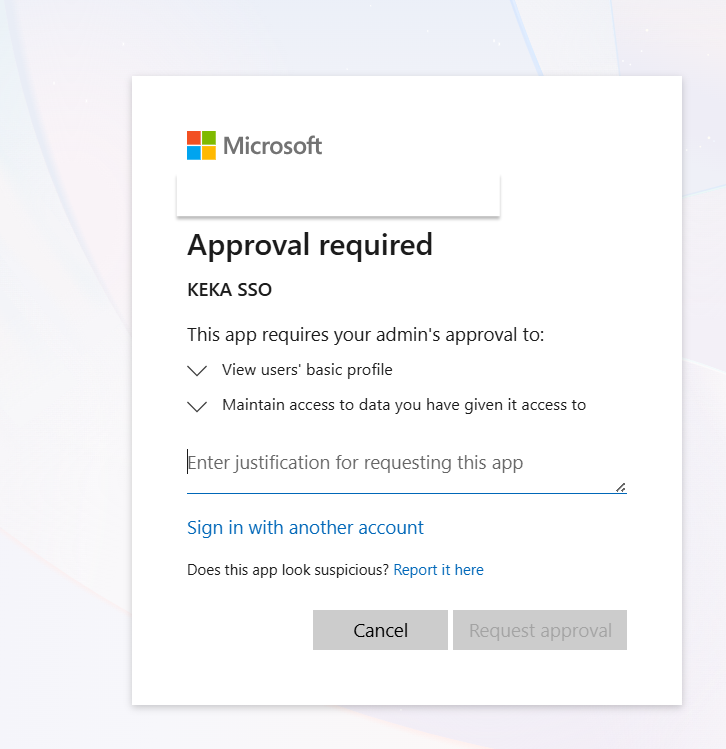
-
Open the Microsoft AD Enterprise app that you have created
-
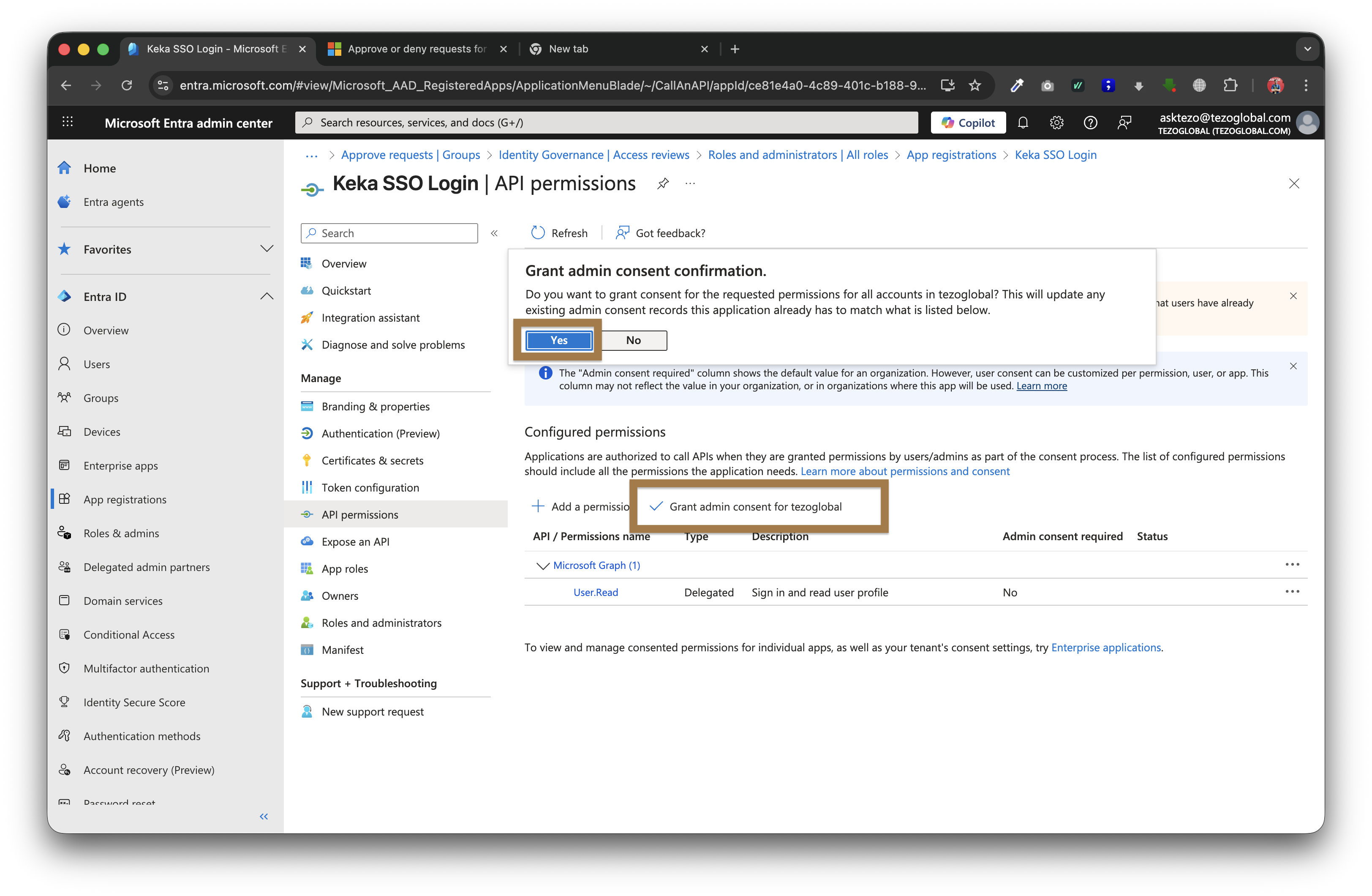
Go to "API Permissions"
-
For some organisations the "Admin consent required" column will have a YES configuration
-
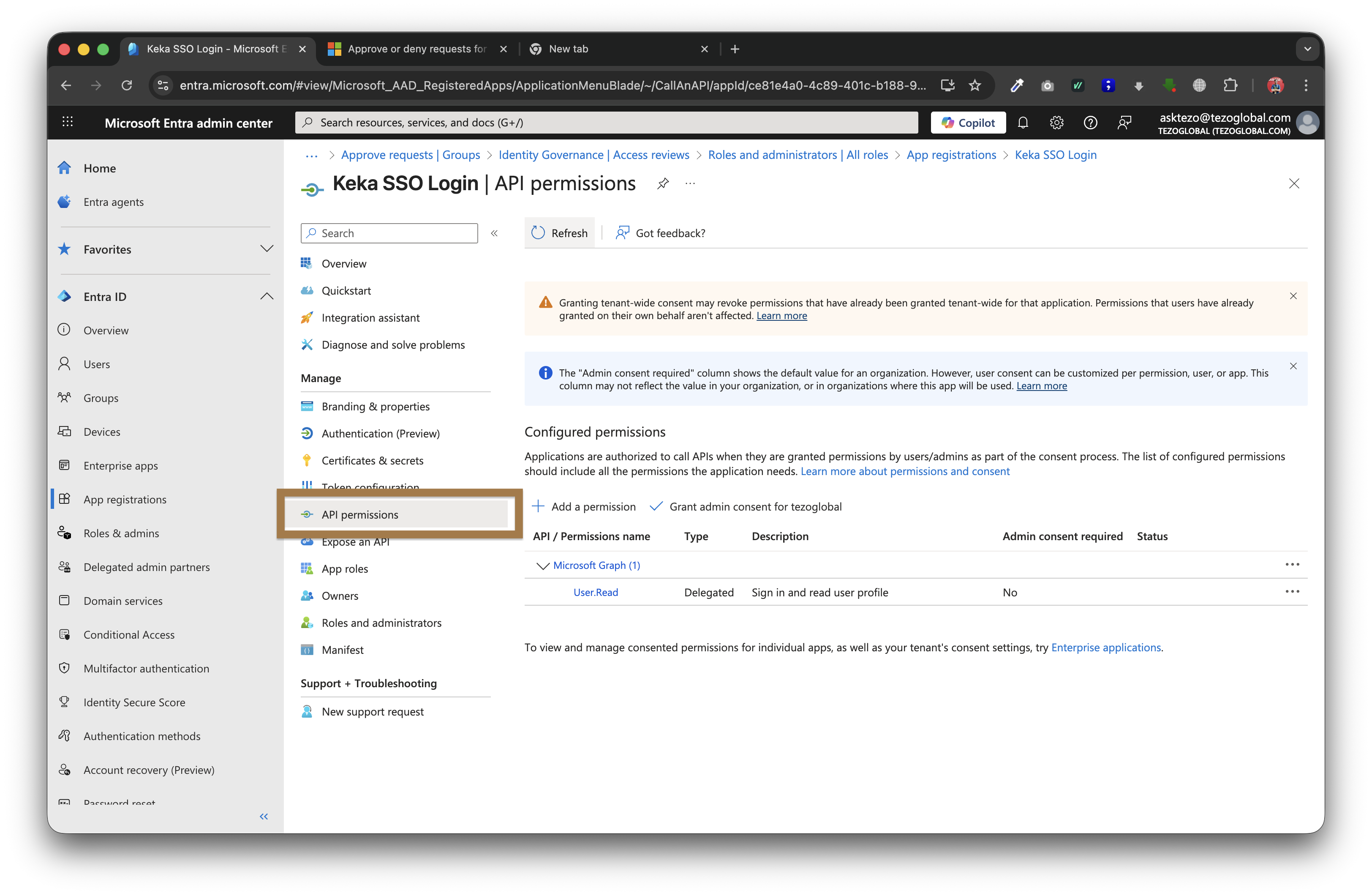
-
Click on "Grand admin consent for org-name"
-
Your employees should now be able to login with Microsoft Azure AD SSO in Keka
Updated 4 months ago